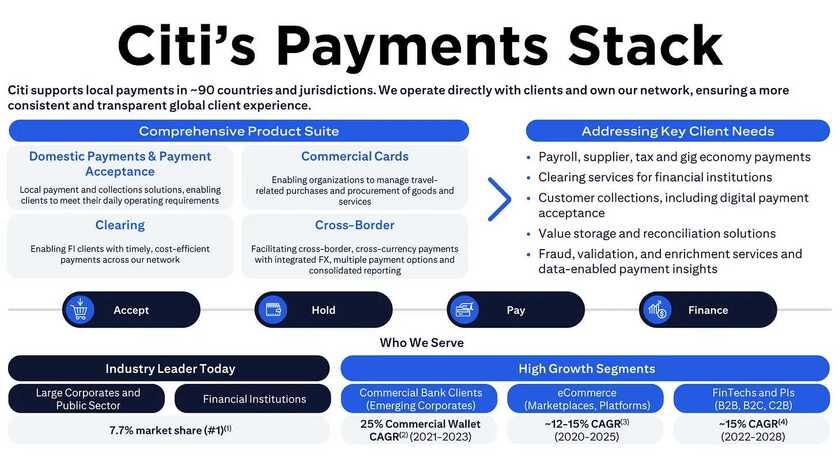
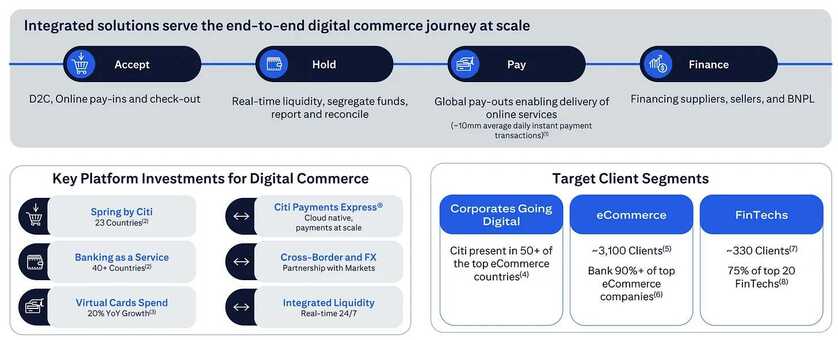
The technique, which claims victims at Twilio and targeted others at Cloudflare, combines text messages intent on luring victims into clicking on a link, leans on the ubiquity of smartphones, seeks to manipulate human nature, and works around an increasingly common defensive measure.
A campaign that relied on the technique gathered steam this summer and targeted more than 130 companies,according to a report from cyberfirm Group-IB last month. The attackers compromised nearly 10,000 user credentials.
The technique works like this:
- Hackers send phony text messages to prospective victims, luring them to click on a link by pretending to be, say, a member of their employers’ IT teamtelling them that their password had expired or their schedule had changed. Typically known as “phishing” when the lures arrive via email, this is known as “smishing” because it’s a portmanteau of “phishing” and “SMS,” commonly known as texting.
- The link leads to a fake Okta site or another tool that verifies a sign-in, known as multifactor authentication or MFA. (Group-IB named the campaign in its report 0ktapus because of the Okta angle.)
- Once the hackers get the code that their victim unwittingly gives them, they’re able to roam around in the victims’ networks.
The Group-IB figures are dramatic, saidRyan Olson, vice president of threat intelligence at Palo Alto Networks’ Unit 42.
“That means they had success on like 70 individuals per company on average, and I don’t know what all the companies are or how big they are, but that was extremely successful for a phishing attack,” Olson told me. “If you were to send a phishing attack over email, you’re lucky if one in a 1,000 people even sees the email and makes it through the filters, let alone click on it, let alone type in their multifactor authentication code as well. That’s a huge amount of success.”
Olson said his company has already seen copycats of the original campaign and expects it to expand, a view others in the cyber field share.
“It’s going to grow,” predictedAngelos Stavrou, founder and chief science officer at Quokka, a mobile privacy company known until recently as Kryptowire.
In most cases, people don’t have as many defenses on their personal phones to block malicious messages as a large organization has on their work emails, Olson said. (Separately, theIRS warned about smishing attacks Wednesday.)
Smishing is a lesser known threat, and people are more accustomed to clicking on text messages, some of which their employer might send,Olson said. And attackers have learned that they can spam requests for MFA log-in codes and some people will eventually give in, which isapparently what happenedinthis month’s Uber breach.
MFA is a well-regarded defensive technique touted by federal officials and major tech companies alike, but as it has grown more common, “MFA fatigue” has taken hold. Often, users just want to make the messages stop and clicking on them is the quickest way.But Olson said you don’t need to be a dummy to fall for the trick.
Often users don’t trigger an MFA request until they sign into a system they use at work. But Olson himself recently got an MFA message because he had timed out of a system that was idle on his computer. Some office workers, in other words, get routine prompts to reauthorize.
For Stavrou, the reason it works is the steady escalation of defense and offense, and how everyday users respond.
“As we become more advanced, the adversary has become more advanced,” he told me. “The information that the user is presented with is increasing faster than they can handle.”
While 0ktapus focused on Okta, Palo Alto Networks has seen campaigns centered on other authentication tools as well, like Duo or Microsoft 365.
There are some limits to the attack method. It requires hackers to use a login code within a certain amount of time, but Olson said that process is likely automated. The overall technique, according to Group-IB and others, doesn’t require major skills.
What can the hackers do to victims if successful? “Recent disclosures reveal that the initial compromises were just part of the attack,” Group-IB noted, pointing to the potential to steal cryptocurrency or use stolen information to launch attacks on other victims.
Some keys tofending off the attacksinclude physical devices like the Yubikey, which make it harder for hackers to intercept identity verification; reliance on apps like Google Authenticator rather than text messages for authentication codes; or employee awareness programs.
Until then, “anytime a technique shows this much success, other threat actors will copy it,” Olson said.



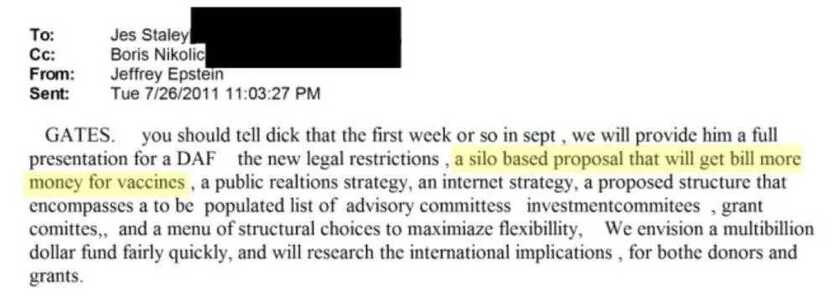
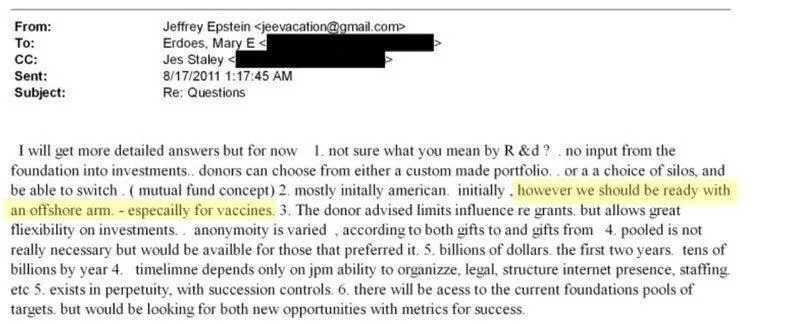

 All while Pfizer—a company with a $2.3 billion criminal fine for fraudulent marketing, bribery, and kickbacks—was given blanket immunity from liability and billions in taxpayer dollars to produce a vaccine in record time with no long-term safety data.
All while Pfizer—a company with a $2.3 billion criminal fine for fraudulent marketing, bribery, and kickbacks—was given blanket immunity from liability and billions in taxpayer dollars to produce a vaccine in record time with no long-term safety data.