(Dinarian Note: This article is from 02/25/22, read it and then go onto the next article from Monday 10/10/22. There are NO COINCIDENCES! And I assure you this is NOT RUSSIA conducting these attacks.. Think Hagelian Dialectic)
February 25, 2022, 2:19 PM
As Russia's military continues to strike Ukrainian cities, national security officials are keeping eyes on a different battlefield.
Senior U.S. law enforcement and Homeland Security officials have told ABC News that there is growing concern that Russia could launch further cyberattacks against the West. 💥The potential targets include electrical grids, banking systems and mobile networks, according to the officials.💥
Currently, there is no cyber threat to the U.S. homeland, according to the Department of Homeland security.
Cybersecurity experts tell ABC News that people shouldn't panic over a potential cyberattack, but they should start preparing for one.

"Freaking out is not a productive thing to do. There are lots of reasons to think that the fact that something is out there but that doesn't mean it could happen," Stuart Madnick, the founding director of Cybersecurity at MIT Sloan, told ABC News. "But there are still a number of things that people can do to stay safe and protected."
Madnick, whose group has consulted with U.S. agencies and private companies such as Nasdaq, said the world is in uncharted territory when it comes to cyber security since this involves alleged cyberattacks by a major superpower. However, what has transpired so far is similar to previous cyber security incidents, he said.
There are two types of cyberattacks, he said: ones that have an indirect impact on people's livelihood and attacks targeting the tech of specific people.
The biggest indirect hacking examples in the past have targeted key infrastructure points such as the Colonial Pipeline ransomware attack in May 2021, which affected everything from gas prices to flights.
"In the last two years, we've been seeing more of these attacks around the world," Madnick said. "You need to realize how many of our systems are connected to computers and just one hack can have bigger effects."
U.S. and international officials have accused the Russian government of committing cyber attacks that targeted Ukraine's banks in recent weeks.
On Friday, Ukrainian officials warned of a phishing scheme emanating from Belarus, which pretended to be a member of the Ukrainian cybersecurity agency.
Javed Ali, the former senior director of counterterrorism at the National Security Council, told ABC News that the attacks could escalate to affect utilities, such as gas and electricity.
"Those will be escalatory steps from Russia and that will also likely be integrated with physical military operations all designed to bring cascading effects against Ukraine," he said.

Madnick warned that cyberattacks on the Ukrainian computer systems could potentially spill over to other regions depending on how close computer networks work.
However, he noted, that U.S. officials are paying close attention to online activity.
Ali said it's hard to predict if Russia would take such an action on the West since it would mean an immediate retaliation from countries with their own state-of-the-art tools and tactics.
"The thresholds for those operations being launched, the effects, [and] the duration those are all things would have to be thought through very carefully," Ali said. "But U.S. Cyber Command is the lead for military operations from the United States, has a world-class capability."
The Department of Homeland Security, the agency tasked with the domestic response to the invasion in Ukraine, has set up a page on the Cybersecurity and Infrastructure Security Agency’s website specifically warning of cyber-attacks emanating from Russia.
Earlier this week, the U.S. Cybersecurity & Infrastructure Security Agency sent an advisory to businesses and organizations urging them to enact a "shields up" guidance.
"While there are not currently any specific credible threats to the U.S. homeland, we are mindful of the potential for the Russian government to consider escalating its destabilizing actions in ways that may impact others outside of Ukraine," the agency said in its letter.
The federal government has called on businesses to make sure their information technology teams update their computer software to close any vulnerabilities and train their employees to watch out for any malware.

Madnick said the preparedness of such attacks varies by sector and their experience as cyberattack victims.
"Organizations like banks that have been targeted for a long time have done a better job in shoring up their cybersecurity," he said. "Others, like hospitals and smaller municipalities that haven’t been attacked in the past tend not to do well."
Madnick said when it comes to individual Americans, there is very little they could do to prevent an indirect attack on the country's infrastructure systems, but they should always prepare for the possibility. He likened it to preparing for a big storm and suggested that individuals who are concerned about their money should always have cash available for emergencies.
Madnick also urged people to back up their important computer files, including bank statements, important e-mails and other documents frequently and to offline sources such as an external drive.
"Everyone should be doing this regardless of increasing cyber threats," he said.
Madnick said cyber attackers linked to foreign agencies wouldn't likely conduct attacks that target individual Americans, but people should still be mindful of the vulnerabilities in their tech. Having updated anti-virus and malware software, staying on top of computer updates and avoiding any suspicious links and e-mails, go a long way he said.
"Cyberattacks and cyber security are not something we talk about a lot, but we need to," he said. "This is not a brand new issue."
----------------------------------------------------------------------------------------------------------------------------------------
Cyberattacks reported at US airports
October 10, 2022, 8:54 PM
Some of the nation's largest airports have been targeted for cyberattacks Monday by an attacker within the Russian Federation, a senior official briefed on the situation confirmed to ABC News.
Importantly, the systems targeted do not handle air traffic control, internal airline communications and coordination or transportation security.
"It's an inconvenience," the source said. The attacks have resulted in targeted "denial of public access" to public-facing web domains that report airport wait times and congestion.
Over a dozen airport websites were impacted by the "denial of service" attack, John Hultquist, head of intelligence analysis at cybersecurity firm Mandiant, told ABC News. That type of attack essentially overloads sites by jamming them with artificial users.
"Killnet," a pro-Russian hacker group, is believed to be behind the attack, according to Hultquist. While similar groups have been found to be fronts for state-backed actors, Hultquist said there is no evidence the Russian government was involved in directing this attack.
The attacks were first reported around 3 a.m. ET when the Port Authority notified the Cybersecurity and Infrastructure Security Agency that the LaGuardia Airport system had been hit. LaGuardia has been restored, but other airports around the country have subsequently been targeted.

The FBI and Cybersecurity and Infrastructure Security Agency, part of the Department of Homeland Security, each said they were aware of the attacks.
The websites for Des Moines International Airport, Los Angeles International Airport (LAX) and Chicago O'Hare International Airport appeared impacted Monday morning.
Later Monday, Denver International Airport, the third busiest airport in the country, was attacked and continues to be attacked, according to an airport spokesperson.
"Similar to many other U.S. airports, DEN’s website has been targeted," the spokesperson told ABC News. "The attacks began around 11 a.m. this morning and they continue. The attackers are attempting to overwhelm our website so that it becomes unavailable to the public."
"At this time, the attacks have not been impactful, though we are closely monitoring these attacks and any others. We are also sharing information on these attacks with TSA, CISA and other airports," the spokesperson added.
Hartsfield-Jackson Atlanta International Airport reported around 10:30 a.m. ET that its site is back up and running and that "at no time were operations at the airport impacted."
"Early this morning, the FlyLAX.com website was partially disrupted," LAX said in a statement to ABC News. "The service interruption was limited to portions of the public facing FlyLAX.com website only. No internal airport systems were compromised and there were no operational disruptions."
LAX said its website was back up and running a little before 1 p.m. ET.
The group "Killnet" has been active since the beginning of the war in Ukraine, targeting Ukrainian allies and recently claiming credit for taking down government websites in the U.S. They operate internationally and have been known to carry out attacks across Europe, according to cybersecurity experts.

Engineers and programmers are actively working to close backdoors that allowed the attacks and shoring up more critical computer infrastructure.
Jamming attacks like the one seen Monday morning are highly visible but largely superficial and often temporary, Hultquist said.
"We are pretty clear it's a Russian cyber group that claimed responsibility," Sen. Chuck Schumer, D-N.Y., said Monday, going on to connect the attacks to the Ukrainian bombing of a bridge in Crimea over the weekend. "We are asking our authorities to confirm who did it and then take the appropriate strong action so the Russians know they cannot get away with this. Putin has a lot of nerve, after his brutal vicious war against the Ukrainian people, to now say he has the right to retaliate because they protected themselves with a bridge is outrageous."






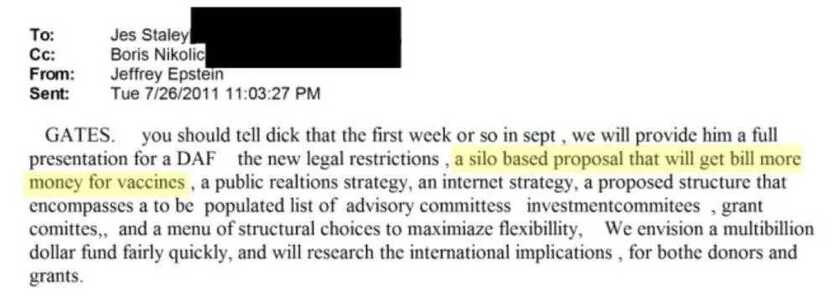
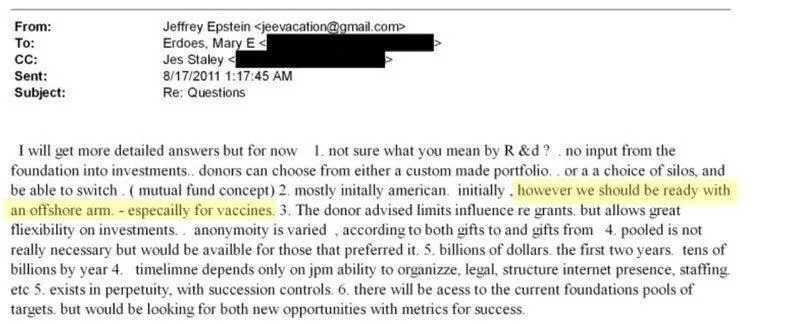

 All while Pfizer—a company with a $2.3 billion criminal fine for fraudulent marketing, bribery, and kickbacks—was given blanket immunity from liability and billions in taxpayer dollars to produce a vaccine in record time with no long-term safety data.
All while Pfizer—a company with a $2.3 billion criminal fine for fraudulent marketing, bribery, and kickbacks—was given blanket immunity from liability and billions in taxpayer dollars to produce a vaccine in record time with no long-term safety data.