(Dinarian Note: Whenever possible, ALWAYS go directly to the source versus clicking on an email link or google ad. Note: When searching on Google, the first 3 or 4 results are ads, do NOT use those. Also, ALWAYS double-triple check your pasted wallet address when withdrawing funds and ALWAYS use a VPN and Antivirus-Malware program, especially when you own crypto. Having cold storage is great, but when sending-recieving funds you are vunerable. Question everything, even if it seems legit.)
Trustwave SpiderLabs uncovered a new strain of malware that it dubbed Rilide, which targets Chromium-based browsers such as Google Chrome, Microsoft Edge, Brave, and Opera.
Rilide malware is disguised as a legitimate Google Drive extension and enables threat actors to carry out a broad spectrum of malicious activities, including monitoring browsing history, taking screenshots, and injecting malicious scripts to withdraw funds from various cryptocurrency exchanges.
Rilide is not the first malware SpiderLabs has observed using malicious browser extensions. Where this malware differs is it has the effective and rarely used ability to utilize forged dialogs to deceive users into revealing their two-factor authentication (2FA) and then withdraw cryptocurrencies in the background. During our investigation into Rilide’s origins, we uncovered similar browser extensions being advertised for sale. Additionally, we found that part of its source code was recently leaked on an underground forum due to a payment dispute.
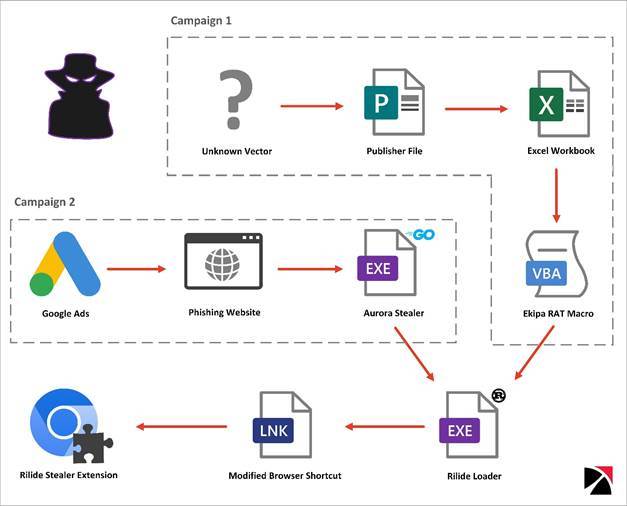
Malicious Campaigns Leading to Rilide Stealer Extension
SpiderLabs uncovered two malicious campaigns leading to the installation of the Rilide extension.
Figure 1. Infection Chains Leading to the Execution of the Rilide Extension
Campaign 1: Ekipa RAT Installing Rilide Stealer
One of the Rilide samples identified by Trustwave SpiderLabs was distributed through a malicious Microsoft Publisher file. This file is part of Ekipa RAT, a Remote Access Trojan (RAT), designed for targeted attacks and often sold on underground forums.
We previously described Ekipa RAT in one of our blogs. It is important to note that Microsoft Publisher was not affected by Microsoft's decision to block macros from executing files downloaded from the Internet. As a result, when a user attempted to open a Publisher file, they would receive a warning but could still enable the execution of malicious content by clicking the ‘Enable Macros’ button. On 14 February 2023, Microsoft issued an update that resolved the Publisher security flaw. With the implementation of the ‘Mark of the Web’ feature on the .pub file, users are now left with only one option, ‘Disable Macros,’ which should have been the case all along.
Any association between the threat actors behind Ekipa RAT and those using the Rilide infostealer remains unclear. However, it is probable that Ekipa RAT was tested as a means of distribution for Rilide, before finally switching to Aurora stealer.
Figure 2. Publisher’s macro and Document_Open procedure executing remote Excel Workbook
Three tasks were configured on the C2 server:
- Download payload from hxxps://nch-software[.]info/1/2[.]exe to %temp% directory as.txt
- Change downloaded file’s extension to .exe
- Execute the payload.
File 2.exe is a Rust-based loader, responsible for installing the Rilide extension for Chromium-based browsers.
Campaign 2: Aurora Stealer Abusing Google Ads
Aurora is a Go-based stealer, which was initially spotted being advertised in April 2022 as a Malware-as-a-Service (MaaS) on Russian-speaking underground forums. The malware is designed to target data from multiple web browsers, cryptocurrency wallets, and local systems.
Recently, the threat actors behind Aurora have been observed abusing the Google Ads platform to spread the malware. According to a report published by Cyble, campaigns mimicking legitimate Team Viewer installers have been utilized to deploy Aurora. As reported by @1ZRR4H and @malwrhunterteam, Aurora was also spread via another campaign that imitated an NVIDIA Drivers installer. A downloaded sample was packed with Themida, a well-known commercial protector for executables. We used the UnpacMe service to unpack the sample.
Figure 3. Aurora campaign imitating the NVIDIA Drivers installer as shown in 1ZRR4H’s Twitter post
Restoring Function Names
The Aurora Stealer sample was stripped of debugging symbols, thus making the analysis harder. Since Go binaries are statically linked, which means that all the necessary libraries are included in the compiled binary, the number of potential functions to analyze is large. However, the original function names can be restored from the pclntab structure, as described in the CUJOAI Senior Threat Researcher Dorka Palotay’s post. Using the go_func.py script for Ghidra we were able to restore the functions names.
How an Aurora Module Downloaded Rilide Stealer
One of the eight grabbing modules, configured in the analyzed sample, contained a base64 encoded blob of data storing the URL for the Rilide Rust-based loader. The payload, hosted on Discord CDN, was saved to the %temp% directory with filename <10-alpahnumeric-characters>.exe and executed via start-process PowerShell cmdlet.
Figure 4. Part of Aurora Stealer routine downloading and executing Rilide loader
The Common Link Between Two Campaigns
The Rilide Rust-based loader samples analyzed as part of the Aurora campaign were packed with a VMProtect commercial packer. After unpacking the samples and analyzing strings contained in the binary, we found multiple references to Windows paths in the C:\Users\ilide\ directory. The same username was observed in the PDB Path of the Rilide sample obtained from the Ekipa RAT campaign.
Figure 5. The same username in a path found in Rilide Rust-based loaders samples from both campaigns.
Rilide Stealer Extension Targeting Chromium-Based Browsers
Rilide leverages a Rust loader used to install the extension if a Chromium-based browser is detected. Rilide mimics benign Google Drive Extensions and abuses several built-in chrome functionalities. The loader modifies LNK shortcut files opening targeted browsers, so that they are executed with parameter --load-extension pointing to the dropped malicious Rilide extension.
Figure 6. Rilide Stealer extension mimicking Google Drive and looking at its manifest revealing the configured permissions
Rilide’s background script attaches a listener to the tabs.onActivated and webRequest.onHeadersReceived events and removes the Content Security Policy (CSP) directive for all requests. This allows the extension to perform an XSS attack and load external resources that would otherwise be blocked by the CSP. The app script adds another listener to the DOMContentLoaded event and retrieves a list of targeted domains from the C2. If the current domain matches any of the listed targets, designated scripts are injected into the webpage.
Figure 7. Configuration list indicating targets such as email services and cryptocurrency exchanges.
Additionally, the background script carries out regular checks on the browsing history and exfiltrates URLs that are matched against the targeted domain list. Moreover, it is capable of capturing and exfiltrating screenshots of the currently active tabs on demand.
Figure 8. Rilide Stealer Execution Flow and Functionalities
Automatic Cryptocurrency Withdrawal
Rilide’s crypto exchange scripts support automatic withdrawal function. While the withdrawal request is made in the background, the user is presented with forged device authentication dialog in order to obtain 2FA. Email confirmations are also replaced on the fly if the user enters the mailbox using the same web browser. The withdrawal request email is replaced with a device authorization request tricking the user into providing the authorization code.
Figure 9. Withdrawal Requests replaced with Authorize New Device emails in Gmail mailbox
Figure 10. Content of the original and forged email. The verification code was extracted from the original message body.
We found no substantial variations in the code between the samples dropped by Ekipa RAT and used in the Aurora Stealer campaign. Both campaigns utilized a Rust dropper, and the functionalities of the browser plugins are nearly the same.
Figure 11. Code differences between Rilide Stealer plugin samples, both using the same C2 server
Rilide Stealer Origins
In the course of our research, we have encountered several stealer extensions for sale that advertised capabilities closely resembling those of the Rilide samples. However, we were unable to definitively link any of them to Rilide. One noteworthy finding was a botnet sale advertisement from an underground forum dated March 2022. Although the advertised functionalities matched those of Rilide, the botnet also included additional features such as a reverse proxy and ad clicker. Notably, the botnet's automatic withdrawal function supported the same exchanges observed in the Rilide samples.
Figure 12. Underground forum post advertising sale of botnet with Rilide-like capabilities
On February 27, 2023, a member of the same underground forum posted a link to the source code for the Rilide extension, reportedly due to an unresolved payment dispute. The leaked source closely resembles that used in the Aurora Stealer campaign but did not contain any of the injected scripts observed in the campaign sample.
Figure 13. Underground forum post, dated February 27, 2023, containing a link to part of the Rilide extension source code.
Notably there is one feature implemented that is missing in the later versions - swapping cryptocurrency wallet addresses in the clipboard. The list of addresses to be replaced is hard coded in the source code.
Figure 14. Clipboard hijacking routine in the analyzed sample from the forementioned forum post.
Pivoting on the Command-and-Control domain ashgrrwt[.]click hard coded in the sample, we identified additional Rilide loaders leading us to the GitHub user gulantin.
Figure 15. Github repository storing multiple Rilide loader and extension samples
Repositories created by this user contain loaders for the Rilide extension, but they are not Rust-based. The sample in the repository named ‘77’ is a .NET extension loader only for the Chrome browser, unlike the later Rust-based version that works for all Chromium-based browsers. Other loaders found in repositories 19 and 789 are based on Advanced Installer – a legitimate Windows Installer Packaging Tool for MSI installers.
Figure 16. Extension loading routine of the custom .NET loader from gulantin’s repository 77
The address contained in the domain variable that is supposed to store the C2 domain suggests that this version of a loader was still under development when submitted to GitHub.
Figure 17. Part of JavaScript configuration in the Rilide extension hosted on GitHub
Conclusions:
The Rilide stealer is a prime example of the increasing sophistication of malicious browser extensions and the dangers they pose. Disguised as a legitimate Google Drive extension, Rilide provides threat actors with the ability to carry out a wide range of malicious activities, including monitoring browsing history, capturing screenshots, and injecting malicious scripts to steal funds from cryptocurrency exchanges.
While the upcoming enforcement of manifest v3 may make it more challenging for threat actors to operate, it is unlikely to solve the issue entirely as most of the functionalities leveraged by Rilide will still be available.
Informational overload can dull our ability to interpret facts accurately and make us more vulnerable to phishing attempts. It is important to remain vigilant and skeptical when receiving unsolicited emails or messages, and to never assume that any content on the Internet is safe, even if it appears to be.
Ultimately, it is crucial to stay informed and educated about the latest cybersecurity threats and best practices to minimize the risk of falling victim to phishing attacks.
Indicators of Compromise:
Publisher File:
File name | Hash Type | Hash |
Tes7777.pub | SHA256 | 0e31ff6406b03982581246b7dd60f3b96edcf0bd007b31766954df001fd68f69 |
SHA1 | e049f56198c23d86e9083142bfe80042e21d4b8e | |
MD5 | 558104b26ccadec3d3eb2925113387a6 |
Aurora Stealer:
File name | Hash Type | Hash |
PackageLauncher.exe | SHA256 | e623984143e0dc6e35c79869ab1521c6714e588e8e648606496f8372ca0d8416 |
SHA1 | b1c100d5a99ae34ccb3654c7b7f8573376a44fd9 | |
MD5 | c28a180de1f80c8c98d0904e64142bef | |
- | SHA256 | ebd72806abd354f3162eec0991d127f993a5dde1a0c719b47087c9ee0edefeaf |
SHA1 | abaaa2644b1e84e8b39119988dd711572377c839 | |
MD5 | 1baaeedd1a26edf4fa79ded370e3d19a |
Rilide Loader:
File name | Hash Type | Hash |
2.exe | SHA256 | 0f11aeecbde1f355d26c9d406dad80cb0ae8536aea31fdddaf915d4afd434f3f |
SHA1 | b4b918a5898463dad1c7d823e0b3f828bac15aad | |
MD5 | 0a4f321c903a7fbc59566918c12aca09 | |
waBp.exe | SHA256 | 8342b134cddeaf34ce05bafa9e860dacf6cd01b85fd00147d90a350516c055e5 |
SHA1 | 25f3fb6d2dab206a5e9b2c0ef26ec6d6a56c5767 | |
MD5 | 561797d7e5cf956e33735180d93be5b6 |
Rilide Extension:
File name | Hash Type | Hash |
background.js | SHA256 | 4cc83be0fa496855d244050616ee2e86b044a9bc87bc5ca70b305986c1ba3bb8 |
SHA1 | 70167e7e5d71fba7d92796324b488c0fb9727712 | |
MD5 | 766d020e902b6470d0510e5c6cfcd6e8 | |
background.js | SHA256 | 55251c725e9f6f51b8db7a631b54dd85b1b59d644c3219e03ceffb0c49cd00a4 |
SHA1 | a39d252e7927ae1adf518e6a3dd08f37e7ee7c26 | |
MD5 | d9cca3dd5bdaeb0466d52821b584602b | |
background.js | SHA256 | 1b01c3e554700e1282c7fdd2dcb54314516ee1f0c5eef3560cdbabc1ba776293 |
SHA1 | ffebf78a9692293a23f9a477ea8a79f7f6ef5aa2 | |
MD5 | 9e5f43b2dc1606e27fa0cfdfb4e363d2 | |
app.js | SHA256 | a28c623d120a76dcfeef9504eaeefabac9d33f292576ccf012fa458b8d7bc6ef |
SHA1 | a46586bfe22f4d84cd9174238740af275bf50c69 | |
MD5 | 740606987f4d588c89d0a5b68648e31e | |
app.js | SHA256 | 8989f4244667626728c6c0083422ff714cb622c92c35a53f9cb1e9891f4528ff |
SHA1 | 5012e783b2ee29cb40b04a10d1a40d0bfda683d9 | |
MD5 | 1c54dd00bc7cc52b60ad4a46e2fb3a77 | |
vpn.js | SHA256 | 170a13a7a8757336babe857804fa24b6cb20aaa9593b32546d7151f23095a510 |
SHA1 | eafdc35b233600ef552b87e684faa3ab3396eae9 | |
MD5 | d54fa225b07298ec34be872cd4ebf4ae | |
manifest.json | SHA256 | bb57a504e0b821552344cecb3da9ecdd0d61817264617a4917d6f5e64a1df7e5 |
SHA1 | 0cb1d9c2a3c8b776ef1e3ec1316fbf595ced7863 | |
MD5 | baee9ba0b94ea1e2b2e566fc8a615554 | |
manifest.json | SHA256 | d70e933e10e667ae7ef6e68a625c447be8aabe9b29affdad999c969bd8769003 |
SHA1 | 84db08e3dcbe40c7cbc998a77788f7303d4a2905 | |
MD5 | 99dc4073f2fe91f48fd16bc65e7dcbc2 | |
binance.js | SHA256 | c8939f8d6237fcc17d486981a800b1e7e9974377de21d7e76677babe8ed536af |
SHA1 | f689396c73055e99a06e002c39e3a74d3d402607 | |
MD5 | 2cc204564b68c5a98b1ff68d861b66c5 | |
bitget.js | SHA256 | 2e310391d77022bcc708c354140319718777ca35efdfb76d6c80cb9de8c8091e |
SHA1 | 05536aa80f8280ddc31be5c0ac3ca995f2190a0a | |
MD5 | 646b9404a29febe9f3741797b79e300c | |
blockchain.js | SHA256 | 4bbb0584eed0c082b5c43d3f259f37cf1a0b64eabb485e85090951a6566d98d4 |
SHA1 | 28ae2440c56350f65b607e4e99b67a2632db873b | |
MD5 | 253f4319673673d2bf5285558a6903df | |
bybit.js | SHA256 | 9dca66f52f31dca921fb238bd36bfc1b1a59d3e4af7b071da9bc4c6bf294e402 |
SHA1 | 61acdad59223a9eb0b392ccd085db1e49700d65 | |
MD5 | 50e363409ba77b20fb6f0bce4eff7b1 | |
coinbase.js | SHA256 | 4df0f18a7e05518bbe93758e751f1f462fef212cdc786c7217d50ddbda14efb5 |
SHA1 | 39f546a4ec94e63e603e3c2481fecab2b5e8a475 | |
MD5 | c1f40584e4ac391d97218ce137a63fb3 | |
ftx.js | SHA256 | ef20c929f5204b223b6e53dc406ea0bcd76d9e98c9ae4942037902883d4bb22a |
SHA1 | 0ead1d32ce6b15c4a90373fce58d1554035cd40f | |
MD5 | ebce63fdc8ef245f117f06ada3ba0f6d | |
huobi.js | SHA256 | e1ad66cc0244fc075e0aabe0fd19502d4c9617829b90aa210e74be1d915275d2 |
SHA1 | 2449e4b27d778f6a4ffc00bb7b73926ac2c54e8a | |
MD5 | 4abe60d2c3506f4767e163d135f89f92 | |
kraken.js | SHA256 | a7f0fdfdfdf1ef65799fd2114bf5c1e133a8b7635b498b334553fbb64b218a05 |
SHA1 | ec6de82efa93e59da148f4d696efcfca851e051e | |
MD5 | b85c5659e946b5d7ad78410356288928 | |
okx.js | SHA256 | 68278b40b59b1b0db2f814d2d864f0b9c2b4285f5795d22cabf60715f922989c |
SHA1 | 415d790b54ca8e374f37fdbb00090110b823ba18 | |
MD5 | ff4e2df1a46d49862ab2a0af830a007e | |
gmail.js | SHA256 | 2f947644c7752ba014eae7971b247be60249a6088923c66ffe9886a7f5c5fe1c |
SHA1 | add0d61399c8c47f8ac73dc83cc83dfa31cddeca | |
MD5 | c0e120778853f0a4865e006a07cd728a |
Phishing Websites:
Malware | Domain |
Aurora | nvidia-graphics[.]top |
C2 Servers:
Malware | Domain |
Ekipa RAT | nch-software[.]info |
Aurora | 45[.]15[.]156[.]210 |
Rilide | vceilinichego[.]ru |
Rilide | ashgrrwt[.]click |
Wallet Addresses:
Cryptocurrency | Address |
BTC | bc1qkczacyp5jq29s5kaphth4asu8cv2y4u4gdgj7q |
BTC | bc1qsjg8dqx6ga30h6szjd8dv2wg50ch50qrey4t7j |
BTC | 1KqequymujeNJuyB4gH7oJSFTB3En3Hf5n |
ETH | 0xDBc1330056E2F5e2FB11FB3C96dE2c44B313eA8d |
LTC | LRYpzmnqBVozkbzJhTWndzYDPfjmNPyaLv |
XRP | rUPTadzFN6LS662Z2d2AvNyqU1xwg2japJ |
TRON | THiD8hFLiEyULVKLp3DSbBXQSbR3MQxm4X |
DOGE | D5asYfjtbTtFmFkrEwqVgbJKYv9YT7Tgjh |





















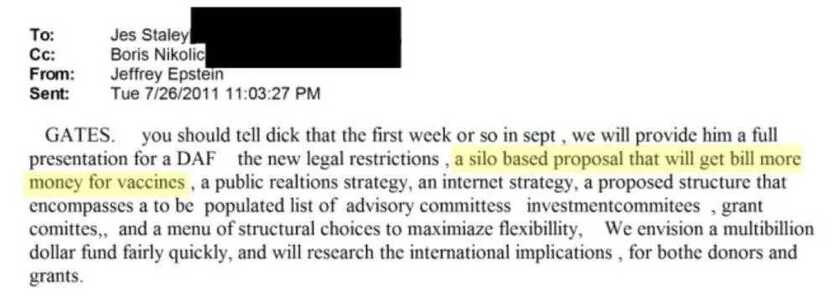
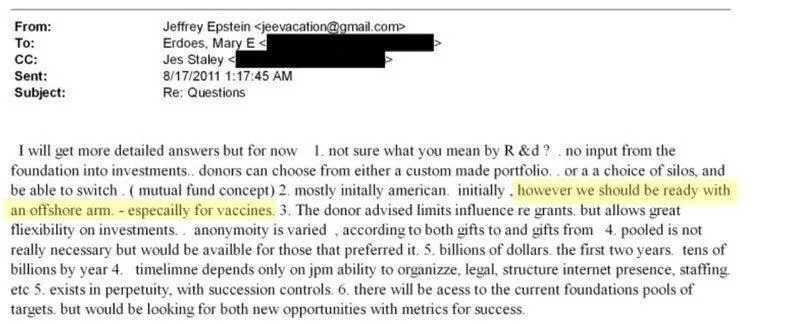

 All while Pfizer—a company with a $2.3 billion criminal fine for fraudulent marketing, bribery, and kickbacks—was given blanket immunity from liability and billions in taxpayer dollars to produce a vaccine in record time with no long-term safety data.
All while Pfizer—a company with a $2.3 billion criminal fine for fraudulent marketing, bribery, and kickbacks—was given blanket immunity from liability and billions in taxpayer dollars to produce a vaccine in record time with no long-term safety data.