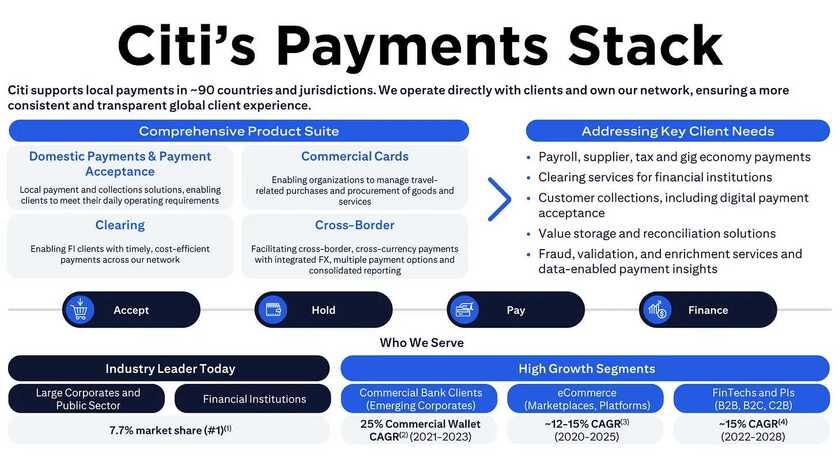
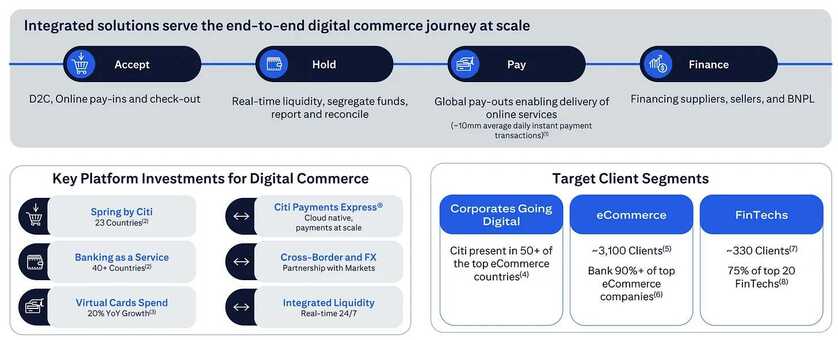
As we wrap up a year of remarkable strides in the world of decentralized finance, The Dinarian family extends warm wishes to each and every one of you! 🚀✨ Happy Holidays and Merry Christmas, dear community! 🎄🎉 May this festive season bring joy, prosperity, and the spirit of togetherness to your lives. As we look forward to a new year filled with exciting possibilities, let's continue building a future where financial empowerment knows no bounds. Thank you for being part of The Dinarian journey! 💙
Every year, hackers get a little more savvy when it comes to scamming people out of their hard-earned money. This year is no different.
What time is better to target the public than the holiday season? It’s a time of year when people are ready and willing to part with their savings and are searching for any offers that may help them get the most bang for their buck.
The holidays are also a time when a lot of people experience feelings of loneliness – they miss friends and family and may struggle with personal situations that could make them more susceptible to cybercriminals. The level of personal and financial vulnerability during the holidays has led to an increase in scam tactics through every possible channel. Unsurprisingly, Black Friday is historically the most popular day for fraud attempts in the U.S.
So, how can you protect yourself and your loved ones this year? You can start by identifying some of the most popular online holiday scams. Keep reading to learn all about them.
UPS Scam: AKA the parcel service scam
“This is ‘UPS.’ We’re going to need your credit card number before we’ll release your package. Just click here…”

Have you received a text message or email that appears to be from UPS, USPS, or another parcel service giving you some “odd” news about a package you may or may not have ordered?
Because this is a time when scammers know people are more likely to order goods online, this con has grown in prevalence.
People receive a message, and often it looks legit. It may be formatted like other parcel service notifications, it can include official logos, and it may even be sent from an email or contain a link that has the company’s name in it. The more legitimate the message looks, the easier it is to trick the recipient into reacting to it.
What happens if you click on the link provided?
There are a few possibilities here.
- Clicking the link downloads some sort of malware into the system of your mobile device or computer, allowing hackers to steal your credentials, access your accounts, and/or collect sensitive information (among other things).
- The link takes you to a page that LOOKS like the legitimate parcel service page. However, there will be a small difference in the URL, content, and other on-site components. Once here, the scammers may ask you for personally identifiable information, account credentials, and even financial information. Then, they have everything they need to steal your identity or gain access to your money.
- The link takes you to a payment page stating that the package cannot be delivered without additional payment. This can be distressing when someone is waiting on gifts for loved ones. When they enter their payment info, hackers take this and use it to fund their own scummy shopping sprees.
According to the FCC, another variation on the scam can cost you money simply by calling the phone number back. The fake delivery notice will include a callback number with an 809 area code or another 10-digit international number. Calling back can result in high connection fees and costly per-minute rates
What can you do to avoid falling for this holiday scam?
The short answer is: Do NOT click through any link sent from a supposed parcel service via email or SMS.
If you HAVE an outstanding delivery, you can always contact the post office or parcel service directly to ask any questions you may have about the validity of messages you receive.
The post office has confirmed that it will never contact you asking you to click any link, so always avoid interacting with unsubstantiated messages completely. If you do receive a suspicious parcel service message, report it to The Federal Trade Commission, and make sure that you block the sender so that you don’t accidentally click through in the future.
FACT: In the first nine months of 2023, people reportedly lost $23.6 million due to text message scams alone.
Visual examples of this scam in action


Additional resources on the UPS holiday scam
Holiday Phishing Scam: The Santa Claus letter scam
“Pay us (and give us your personal info) and we’ll send a custom Santa letter to your kid. Or not…”

This scam is every bit as despicable as it sounds. When the holiday season hits, parents look for ways to make it as special and memorable for their children as possible. What better way to bring magic into the Christmas season than a customized letter sent courtesy of Santa Claus?
Unless “Santa” in this case is really a scammer who’s pulling on your heartstrings to get to your wallet.
These scammers will use several channels to try and fool people into giving them money. They may send advertising emails directly to your account, use paid advertising channels, place ads on social media, contact people via SMS, and sometimes create legitimate-looking websites to make targets feel more comfortable about putting in their payment info.
They advertise a custom “Santa letter” service that offers to send special communications to children on behalf of Mister Claus. This service will usually have a pretty reasonable cost and may offer variations like emails, texts, or even phone calls from the big man himself.
However, once parents put their payment info in for the service, the Scam Santa never delivers.
What happens if you give the Santa scammers your info?
As soon as your financial info is put into their system or shared with them, criminals take the financial info and help themselves to as many “presents” as the bank account can afford.
This can lead to several problems, including (but not limited to):
- Hijacking the bank account and using the money to make purchases
- Opening new accounts in the victim’s name
- Identity theft
What can you do to avoid being taken advantage of by this holiday scam?
Be very cautious when considering setting up Santa letters for your children. Make sure that the company has been around for a substantial amount of time, check the activity on their social media accounts, and make sure to read reviews across multiple sources about the brand. It’s easy to fake reviews in just one place, but more difficult to do so across all channels.
If you want to simply send a customized letter to your child yourself, the postal service has some simple instructions for doing so that will make the experience just as magical. You can find that info by clicking here.
Santa Letter holiday scam example:

Additional resources on the “Santa Letter” holiday scam
The “seasonal work” holiday scam
“Need a job this season for gifts? We know, and we’re going to use it to take advantage of you…”

Everyone needs more money, but this is especially true during the holiday season when the pressure to provide gifts for people you care about overrides budget plans.
Scammers know this, and they’ve learned how to take advantage of it. Beware of seasonal work offers that sound way too good to be true. Criminals use false advertisements on job boards, emails, and social media to draw people who need temporary work.
These criminals have become more sophisticated today – they create professional-looking websites and run ads for seasonal work. When someone clicks through the holiday job posting, they are redirected to a website that looks legitimate. In reality, this site is just a front being used to collect sensitive personal data.
People offer up their social security numbers, addresses, direct deposit information, and other information, all while believing that it’s required for a job application. But when it comes time for them to hear back from the company, the website will have disappeared–taking all of their personal information with it.
What happens if you give the holiday scammers your private information?
If scammers are successful at collecting your personal information, they can use it for identity theft, bank fraud, credential stuffing attacks, and several other nefarious activities. Occasionally, they collect this data and sell it on the dark web to the highest bidder.
This can be a scary scenario and leaves many feeling like they’ve had the rug pulled out from under them. It’s especially damaging for those who experience financial losses at a time of year when they are trying to do holiday shopping. It can take a long time for banks and credit card companies to iron out identity theft issues, leaving many victims in a bad spot that can have a lasting impact on their credit.
What can you do to avoid being taken advantage of by the “seasonal work” holiday scam?
Fortunately, there are several steps you can take to protect yourself from becoming a victim of the seasonal work scam.
- Before providing any potential employer with personal information, check out the company’s history. Make sure that it is an established brand and is registered as a business.
- It’s also a good idea to check multiple sources for reviews to spot any hidden issues.
- When directed to the website of a familiar brand to apply for a position, make sure that the URL matches the one used by the legitimate company.
- When in doubt, reach out and ask questions.
- As a rule of thumb, if it looks too good to be true and offers high pay for minimal work - proceed with extreme caution!
- No legitimate job should require you to pay to work for them. If you are asked to send money or cash a check once “hired,” stop engaging with the “company” immediately.
Visual examples of this holiday scam


More resources on seasonal work holiday scams
The “website spoofing” holiday scam
“Check out great deals from trusted brands - at a slightly different URL, with blurry images and too-good-to-be-true pricing. Wait…”

Deals can be everything this time of year. But as we’ve said before, if it’s too good to be true…it’s probably a scam. This becomes apparent when you get an email from your favorite brand, click on the link, land on a legit-looking site, give them your payment info, and then never hear from them again. Oof.
Website spoofing is a more complicated form of phishing that occurs when a scammer mimics the style of a trusted brand to create a website that looks like a legitimate part of that brand. They’ll use logos, steal content off of the site, and even place copyright claims at the bottom of the page. All to fool people into giving them personal information.
They may link to these sites from ads, emails, and/or social media posts, and their goal is to make everything look as consistent and trustworthy as possible. Oftentimes, scam artists will use a hook to draw consumers in.
This may be something like: “Fill out this survey and get a free high-end product,” or “Click this special sale link and get everything at 75% off.” The goal is to do whatever it takes to convince the recipient to click through to the fake website.
Once there, the site may contain a survey, a product page (copied from the legit site), or some other enticing deal designed to part you and your hard-earned money.
What happens if you give the website spoofers your information?
When people follow through with a purchase, survey, or membership on one of these spoofed sites, they often provide their full names, addresses, phone numbers, email addresses, and financial information. If asked to “create an account,” the scammers may also save these credentials and use them in a future credential-stuffing attempt.
FACT: Credential stuffing involves taking a set of credentials and applying them to different accounts to try and gain access to someone’s personal information.
The info collected from spoofed websites can be used for identity theft, financial fraud, or sold on the dark web to the highest bidder. This can result in scammers passing personal info to other scammers who then incorporate it into future phishing, robocalling, or other types of cons.
Once your information is accessible, it can be very difficult to track down the original point of the data leak.
What can you do to avoid being taken advantage of by the website spoofing holiday scam?
While it can be admittedly difficult to discern a fake site from a legitimate one, there are some red flags to look out for. If you see any of these signs, don’t click through the links. Instead, navigate straight to the verified brand URL and look for the same deals there.
If they don’t match, then it’s more than likely a scam.
Keep an eye out for this website spoofing tricks over the holidays:
- An email flier that comes via your spam box directing you to a well-known branded website
- Any email or ad that has poor spelling, minimal content, bizarre formatting, and low-quality images
- Ads for deals that are too good to be true or selling items that your favorite brand doesn’t usually carry
- A website URL that doesn’t align with any of the sites associated with the real brand
- Links on the website to content that doesn’t exist or that take you in a continual loop back to the home or sale pages
- Offers declaring you a “winner” for something you did not sign up for
- Sites with poor images and layouts that look rushed and unprofessional
- Sites that ask you for excessive personal information just go “enter a contest,” or “qualify for a deal”
- Sites claiming to be a subsidiary of a trusted brand that are “only available” over the holidays and that do not have a URL consistent with the verified one
If you’re ever in doubt about the validity of a site or deal, go straight to the source and only buy from brands and websites you know you can trust.
Example of a website spoofing a holiday sale

Additional resources on website spoofing scams
- More info on phishing and spoofing
- Report suspected scams
- National Cyber Security Centre
- Cybersecurity and Infrastructure Security Agency
Holiday phishing scams
Wow! This email from [email protected] promises designer brands for Wish prices! I just need to give them all of my personal information…”

‘Tis the season for gargantuan shopping excursions. Unfortunately, scammers are out in droves to take advantage of eager holiday spenders. Consumers who are doing their shopping online are often inclined to create new accounts, sign up for discounts, and activate memberships in pursuit of the hottest gifts of the year.
With all of this happening, it’s easy for people to forget what companies they’ve shared their email addresses and phone numbers with. So, it may not feel out of the ordinary to suddenly see an inbox full of sales emails, or a few new SMS messages a day offering “special limited time” discounts.
While the spam feature on your inbox may catch the majority of these phishing emails, there are always some that find their way into your primary inbox. They may contain flashy subject lines claiming unreal discounts, free trials, contest entries, and even indicating that you’ve “won” something from their company. In some cases, these can be the beginning of a website spoofing scam.
On the flip side, scammers also recognize that this is a time of year when many people connect with family and friends. It’s easy for a con artist to find the names and locations of your family members online and then send emails pretending to be these people.
They may make personal-sounding email addresses or try and text from a “new number” to get you to engage with them. Oftentimes, they try to sound very personal from the very beginning in an attempt to capitalize on the rapport of an existing relationship.
Then, they may provide a sob story about a “sudden illness,” or an inability to pay for basic necessities during the holidays. The goal of this type of holiday phishing scheme is to convince you to send them information or money in a way that exposes your financial information.
Once they have this, they’ll do their OWN holiday shopping at your expense.
What happens if you give the scammers your info?
Similar to website spoofing (the two often overlap), the bad actors in this holiday phishing scam will collect personal information with the intent of using it for financial gain, identity theft, or to sell on the data black market. In some instances, they may even try to take advantage of the victims multiple times, often pretending to be family members, charities, or people in need, and asking for money on more than one occasion.
At best, people figure out what’s happening before it goes too far. At worst, they can lose their life savings by voluntarily sending money to people or companies under deceptive circumstances.
What can you do to avoid being taken advantage of by this holiday scam?
There are several things you can do to protect yourself this season:
- Check the sender addresses of every email you receive that you don’t immediately recognize. You can perform a quick online search to check if the format of the email matches the format used by the brand it’s being associated with. If the formats don’t line up, it’s a good idea not to respond or click through any links within the text.
- Never send money to anyone who reaches out via email, social media messengers, or through an unknown SMS number. If the sender is claiming to be someone you know, reach out to the person to verify that the communication is legitimate.
- Avoid clicking any links contained in emails that land in the spam box.
- Do not click on links or respond to SMS messages claiming to be from people who aren’t verified or companies you haven’t signed up with.
- Beware of any email or text asking for personal information - especially when the amount of information feels disproportionate to the situation or unnecessary.
- Always verify that websites and phone numbers are consistent with any brands they claim to be associated with. Reach out to companies to verify before engaging with the messages.
- Watch out for poor grammar and spelling, low-quality images, and/or strange formatting that wouldn’t make sense coming from a well-known professional brand.
Visual examples of phishing scams

Additional resources on holiday phishing scams
- The Federal Bureau of Investigation
- Information from the Attorney General
- The Federal Communications Commission
Help! I already shared my personal information in a potential holiday scam.
If you feel that you may have already shared your personal data with scammers this holiday season, it’s important to catch it as early as possible. The following resources can provide you with additional information and agencies where you can check your identity theft status and report data leaks.
- What to do if you were scammed (FTC)
- How to spot and report identity theft
- The Consumer Financial Protection Bureau (more on identity theft)
- Information on credit monitoring
- The Elder Fraud Hotline







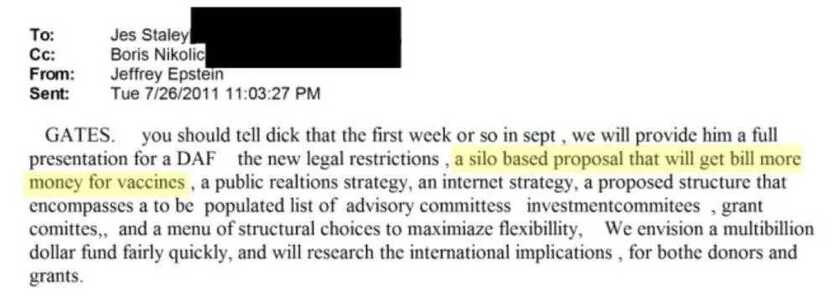
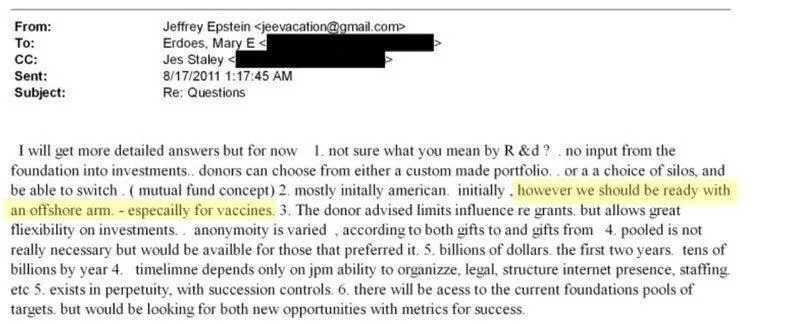

 All while Pfizer—a company with a $2.3 billion criminal fine for fraudulent marketing, bribery, and kickbacks—was given blanket immunity from liability and billions in taxpayer dollars to produce a vaccine in record time with no long-term safety data.
All while Pfizer—a company with a $2.3 billion criminal fine for fraudulent marketing, bribery, and kickbacks—was given blanket immunity from liability and billions in taxpayer dollars to produce a vaccine in record time with no long-term safety data.