Phish of the week: Symbiotic X account is compromised
According to a report from PeckShield, the X account for the staking protocol Symbiotic was hacked on Oct. 5. The team’s official website said the account was still compromised as of Oct. 7.
The compromised account promotes a “points” checklist and asks users to click on a link to check how many points they have. However, the link leads to the wrong URL, network-symbiotic[.]fi, instead of the correct one, symbiotic.fi.
Phishing post from Symbiotic X hacker. Source: Symbiotic.
When users connect to the fake phishing site with a wallet, they are presented with a page that claims they have earned thousands of points, even if they have never interacted with the Symbiotic protocol.
The page urges users to redeem their points immediately and claims they will be lost if they do not click a large, green, “redeem” button in the middle of the screen.
Fake Symbiotic site allegedly used for phishing attacks. Source: network-symbiotic.fi
Pushing the “Redeem Points” button with an empty wallet results in an error message stating that the user should try a different wallet, with a standard error message found on phishing sites asking for message signatures.
If a user’s wallet contains Symbiotic tokens, the site likely asks the user to sign a message, which is then used to drain the user’s tokens. Cointelegraph did not test the app with a wallet that had funds in it.
From its official website, the Symbiotic team is currently warning users that its X has been compromised and that users should not interact with any sites linked to the account.
Symbiotic warning of compromised X account. Source: Symbiotic.fi
X account hacks have become a routine problem in the crypto space. Users should consider bookmarking the URL for apps they frequently use, as this is generally a more reliable way of getting to the correct website than relying on X links, although it is not 100% foolproof either. Users should be especially cautious when asked to sign a message written in code, as this is often, but not always, a sign of a phishing attack.
Malware corner: Attackers now using SVG files to lure victims
Attackers are now using SVG image files to infect victims’ computers, according to a September report from HP’s Wolf Security team.
⚠️The new method allows attackers to gain control of a victim’s computer through remote access trojan (RAT) software. Once the software is installed, the attackers use it to steal the victim’s website passwords, seed words, and other personal information. If the user owns cryptocurrency, these credentials are then used in further attempts to gain access to the user’s wallet and empty it.⚠️
Researchers found that the malware was disguised as a ZIP archive that loaded when the image was opened in a browser. It also featured a .pdf file that loaded as a distraction for the victim while the malicious program was being downloaded and installed in the background.
According to Adobe, Scalable Vector Graphics (SVG) files store images “via mathematical formulas based on points and lines on a grid” instead of through pixels. This means that they can be easily resized without losing their quality. In addition, they are written in XML code, which allows them to store text inside of themselves.
According to Mozilla, SVG files also contain a “script” element that allows developers to embed executable programs within them. It is this scripting ability that the malware developers have reportedly learned to abuse.
HP researchers found an image that produces a ZIP archive when opened in a browser. If the user clicks on the archive, it opens a File Explorer window and begins to download a shortcut file.
Clicking the shortcut causes a decoy .pdf file to load on the victim’s screen. Meanwhile, the device begins to copy various scripts and store them in the victim’s music, photos, and startup directories, allowing the program to persist over time.
Malicious URL file in infected SVG and decoy .pdf meant to distract the user—source: HP Wolf Security.
⚠️After copying these scripts onto the device, it runs them. The result is that a number of dangerous malware programs, including VenomRAT, AsyncRAT, Remcos and XWORM, are installed on the user’s device. Once the malware is installed, the attacker can take full control of the victim’s computer, swiping any files held within it.⚠️
Given this new attack vector, crypto users should exercise caution when interacting with SVG image files from sources they do not entirely trust. When opened, if an image loads other types of files, users should consider rejecting these files by closing the browser window.
Fire token exploit illustrates risks of novel tokens
Buying new tokens with novel features and unaudited contracts is often risky, as is illustrated by what happened to the FIRE token on Oct. 1.
The Uniswap pool for the token was drained of nearly all of its liquidity after an attacker exploited the token’s contract to repeatedly sell it at a higher and higher price each time.
After the exploit, the token’s team immediately deleted their social accounts and vanished, implying that the project may have been a rug pull or exit scam from the start.
The token has not traded since Oct. 2, which implies that there may be so little liquidity for it that selling may be impossible.
The idea presented to FIRE investors was simple. According to its website, it was an “ultra-hyper-deflationary token.” Whenever holders sold their FIRE into the token’s Uniswap liquidity pool, it would automatically be sent to a burner address. This would cause the token supply to shrink, driving up the value of the FIRE held by those who didn’t sell.
Fire token website. Source: Fire.
The token was launched at 8:00 am UTC on Oct. 1. About 90 seconds after the launch, an account ending in 1e2e drained some $22,000 worth of Ether ETH
To accomplish this, it first took out a flash loan of 20 ETH from the lending platform Spark Protocol. Then it created a malicious contract that swapped the ETH for FIRE, then swapped it back, destroying the newly acquired FIRE in the process and raising its price.
This process was repeated through 122 transfers through 16 different smart contracts, with each transfer being part of a single transaction. Each time FIRE was swapped for ETH, a slightly larger amount of ETH was received in return. As a result, the attacker was able to drain the pool of the $22,000 worth of ETH. In addition, this transaction destroyed 230 FIRE tokens.
The attack was repeated over and over again, with the final exploit transaction taking place on Oct. 2 at 1:14 am UTC.
Blockchain security platform TenArmor reported the attack on X. “Our system has detected that #FIRE token @Fire_TokenEth on #ETH was attacked, resulting in an approximate loss of $22.3K,” the post stated.
Source: TenArmor.
According to price data from tthe rading platform Apespace, the initial price of FIRE was set at approximately 33 ETH ($81,543 at current prices) or around $8 per 0.0001 FIRE. At the moment of the exploit, the price of FIRE skyrocketed, increasing to 30 billion ETH per coin or $244.6 billion per 0.0001 FIRE. It then fell to 4.7 billion ETH per coin over the next two minutes.
Note that by the time these high prices were reached, significantly less than one FIRE coin remained in circulation, as most of the token’s supply had been destroyed in the exploit.
FIRE one-minute chart showing exploit at approximately 8:13 am. Source: Apespace.
After the exploit, the FIRE team deleted its X and Telegram accounts, which suggests that the attacker may have been affiliated with the team. The token’s Apespace page also features a warning that the FIRE contract contains a “blacklisting” feature allowing developers to blacklist any user’s account and prevent them from selling the token. The developers may have used this blacklisting feature to only allow themselves to sell.
Users should exercise caution when interacting with tokens that have novel features that may not be fully understood.
In this case, the developers explicitly stated that anyone who sells into the pool destroys tokens, reducing their supply. Still, some users may not have realized that this allows a single trader to repeatedly swap into and out of the token to artificially raise its price and drain its liquidity.







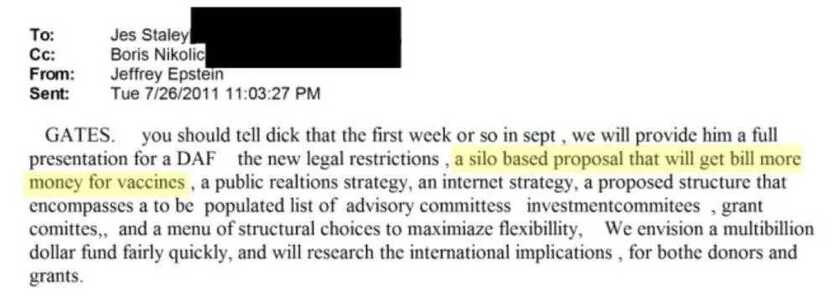
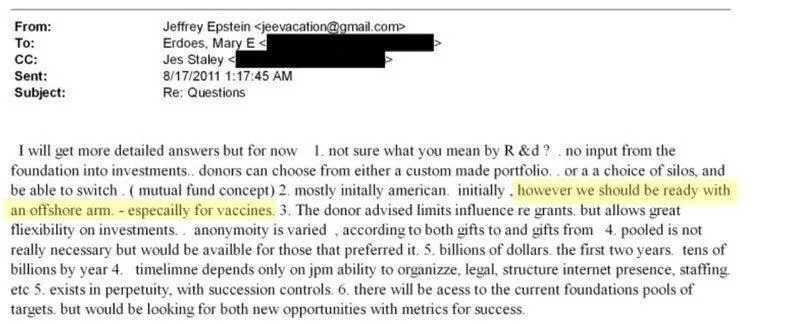

 All while Pfizer—a company with a $2.3 billion criminal fine for fraudulent marketing, bribery, and kickbacks—was given blanket immunity from liability and billions in taxpayer dollars to produce a vaccine in record time with no long-term safety data.
All while Pfizer—a company with a $2.3 billion criminal fine for fraudulent marketing, bribery, and kickbacks—was given blanket immunity from liability and billions in taxpayer dollars to produce a vaccine in record time with no long-term safety data.