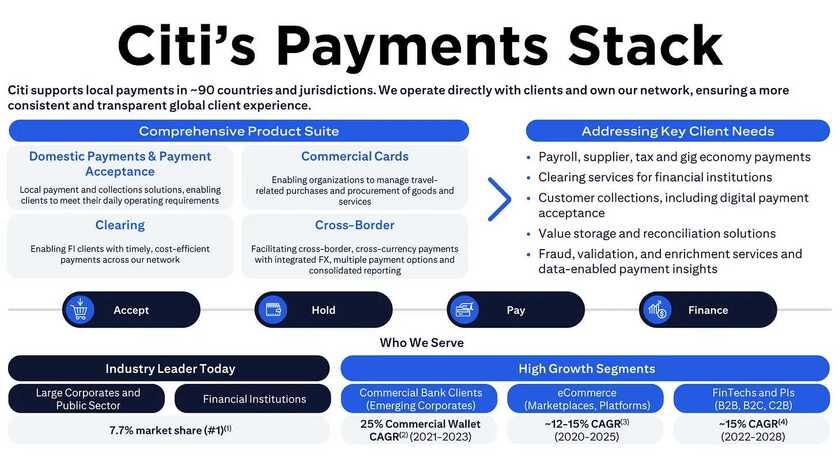
It has been two weeks since Bybit was hacked to the tune of $1.4 billion by North Korea’s TraderTraitor. Five days later, it was confirmed that the hackers compromised a SAFE Wallet developer, allowing them to alter the wallet’s user interface source code. Now SAFE has released its own preliminary investigation, reconfirming that the wallet smart contract was never compromised, but the user interface was.
SAFE hired Mandiant, the security firm acquired three years ago by Google Cloud for $5.4 billion. The wallet organization also outlined a number of steps it’s taking to shore up security, with Mandiant’s help.
As previously noted, the hackers injected code into the user interface, which only impacted Bybit. While other users would have accessed their wallets with the same compromised code, it did not target them.
SAFE reiterated the need for people with the authority to sign transactions to fully understand what they sign, as highlighted by custody tech firm GK8 in a recent webinar. In the transaction at the root of the hack, one obscure parameter was switched from zero to one, with dire consequences.
Step 1: Hack the developer’s machine
The report is slightly vague about the initial hack of the developer’s machine, partly because the malware was removed. However, Mandiant believes it involved a specific docker project (an executable software container) related to stocks that the developer may have downloaded as a result of social engineering. (Couldn’t the developer confirm this?)
Mandiant cites another recent hack by the same group where they lured a developer into providing technical assistance. To do so, they shared a docker container which was downloaded by the engineer, with the software enabling the hacker to have ongoing access to the workstation.
Step 2: Access the AWS code repository
The hacker compromised the hacker’s machine on Feb 4 and first accessed the Amazon Web Services (AWS) code repository on Feb 5. However, they wanted to have sufficient access to the repository to be able to manipulate it without being noticed. AWS generally advocates multiple authentication methods, so the hackers attempted to add their own Multi-factor authentication (MFA) device, but failed.
They spent the next 12 days monitoring the AWS environment and planning next steps. For accessing a web server including committing code to a repository, AWS provides temporary session tokens which expire after 12 hours by default. The hackers hijacked these tokens in order to insert their own code. They used a virtual private network to do so.
Step 3: Inject the malicious code
The malicious code was injected into the AWS repository for the user interface on February 17. So people were using the hacked code for four days. However, the code was only targeted at Bybit’s wallet address, so it would not have impacted anyone else.
Step 4: Wait to hack. Remove the malware post hack
We already published an article about the specific transaction that was hacked on February 21, which was not part of yesterday’s SAFE report. The hacked code switched a parameter called “Operation” from zero to one, allowing the hackers to do as they wished with the funds.
According to Mandiant, shortly after the hack, the hacker removed the malware. Unix machines keep a log of every command performed, which would have helped to monitor the hacker’s activities, but that log was also wiped clean. Hence, we’re guessing Mandiant mainly used network logs and AWS activity logs. By covering its tracks, the hackers likely hope to re-use some of the same methodology in future breaches.







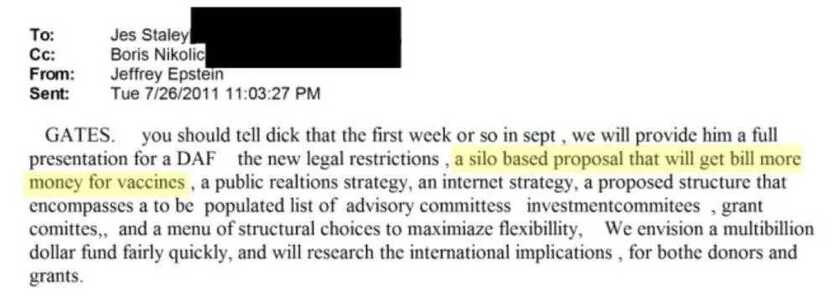
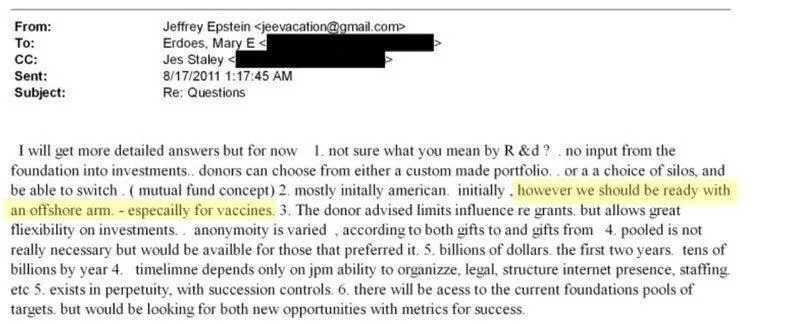

 All while Pfizer—a company with a $2.3 billion criminal fine for fraudulent marketing, bribery, and kickbacks—was given blanket immunity from liability and billions in taxpayer dollars to produce a vaccine in record time with no long-term safety data.
All while Pfizer—a company with a $2.3 billion criminal fine for fraudulent marketing, bribery, and kickbacks—was given blanket immunity from liability and billions in taxpayer dollars to produce a vaccine in record time with no long-term safety data.